Enterprise-level secret rotation for Azure environments.
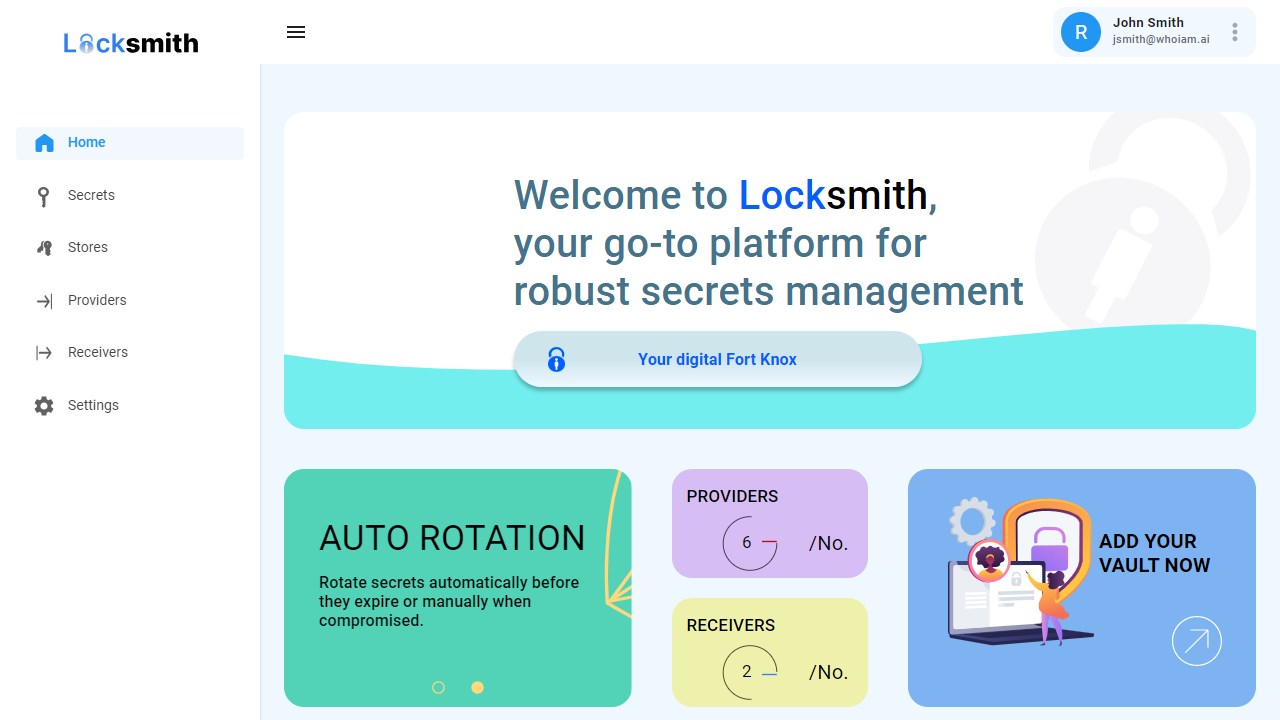
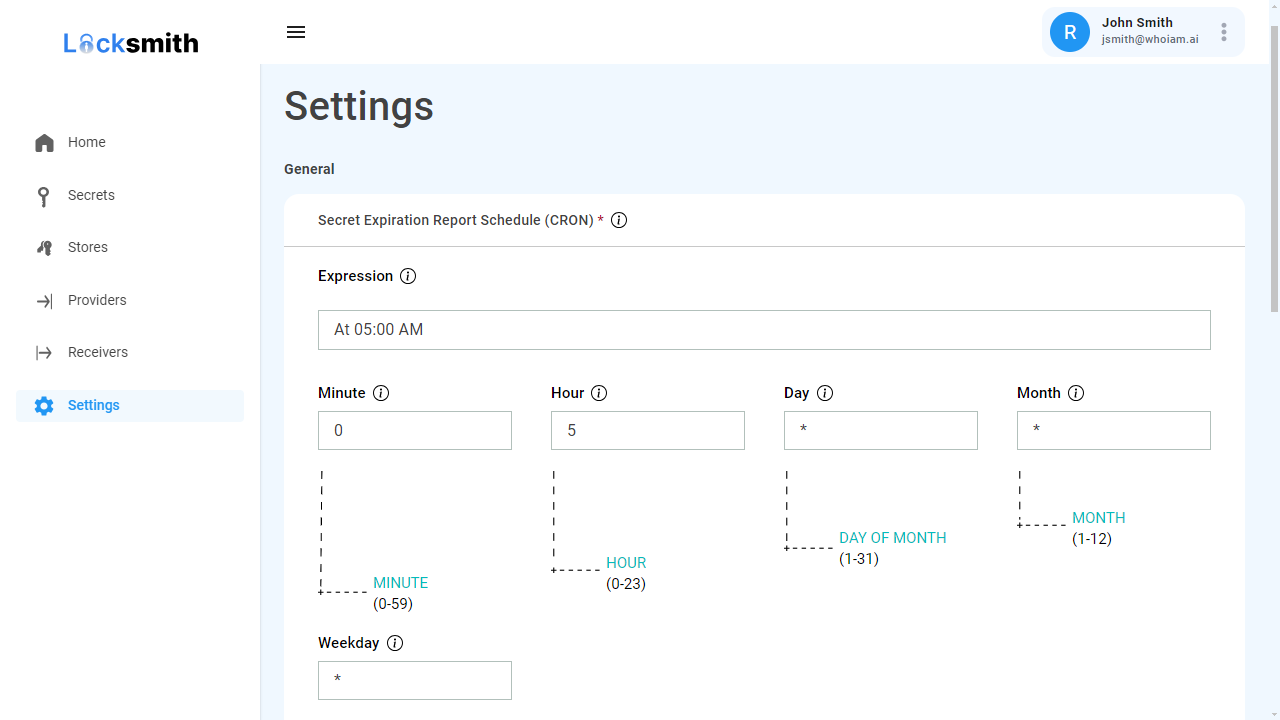
WhoIAM Locksmith brings enterprise-level secret rotation to Azure environments, particularly focusing on identity and access management (IAM) platforms such as Microsoft Entra, Entra External ID and Azure AD B2C. It provides secret expiration notifications, automatic key vault secret replacement, and interconnected system configuration updates.
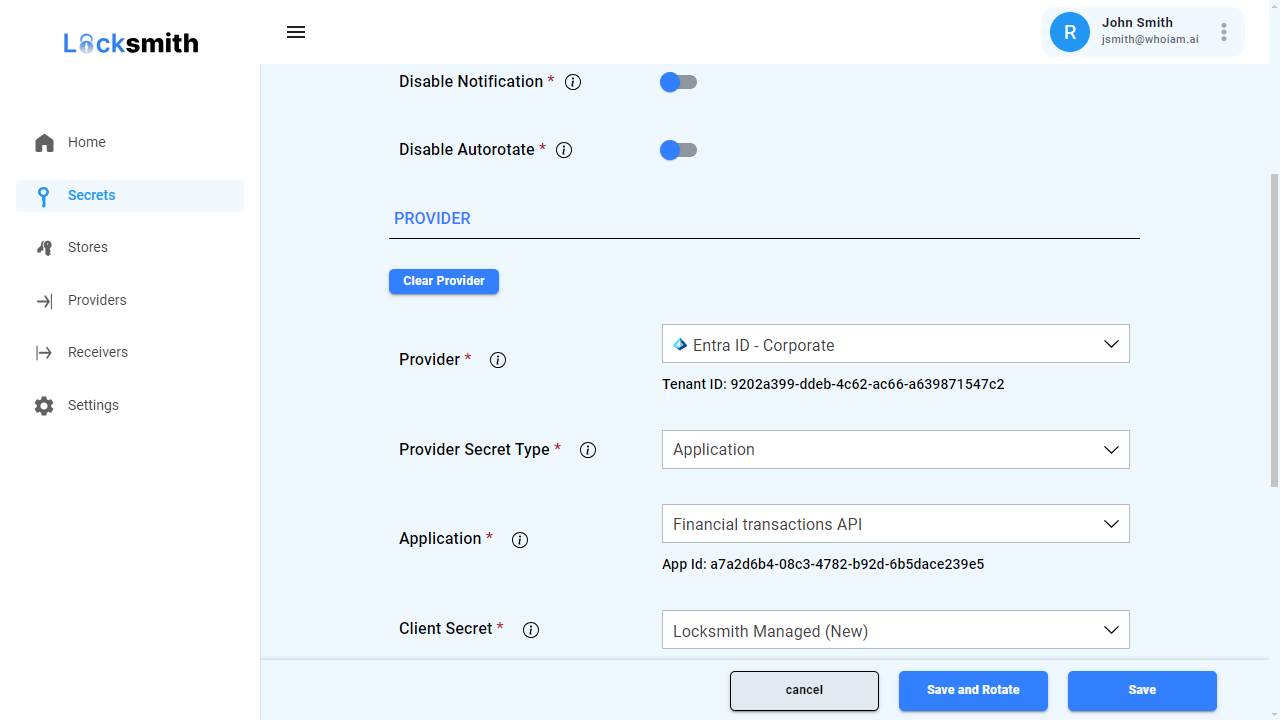
System-to-system communications are often secured using secrets (e.g. certificates, keys and passphrases). For example, web apps use certificates and passphrases to authenticate and encrypt traffic to databases, APIs and other downstream services. Similarly, Entra External ID and Azure AD B2C rely on certificates and keys to secure communications to federated identity sources, email providers and external identity APIs.
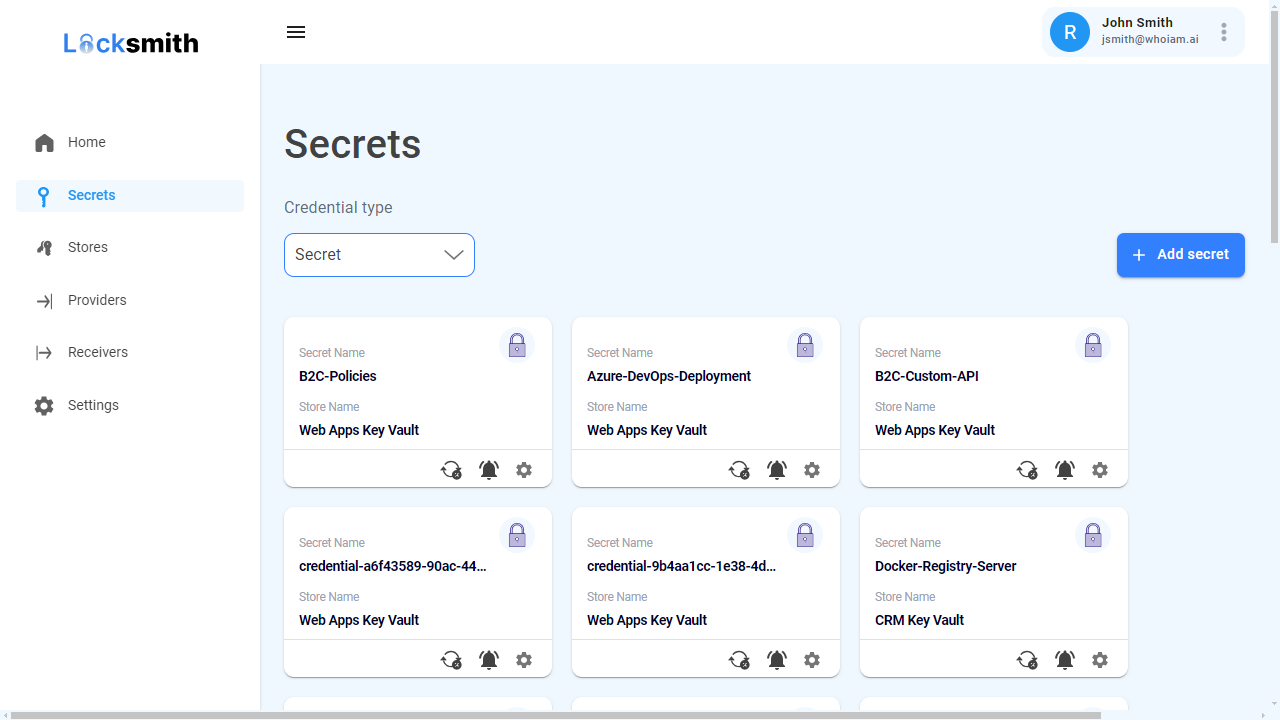
It is best practice to rotate secrets (i.e. set expiration dates and replacing them periodically) to reduce operational and technological risks if they are compromised. A common challenge when rotating secrets is to update configurations in all interconnected systems in a timely manner. For instance, system downtime can occur if configurations are not updated before a secret expires, often leading to important operational costs. Also, if rotation is managed manually, a user with high administrative privileges needs to replace secrets and update all interconnected systems. This process introduces administrative burden and increases security risks by requiring high-privilege wide-scope administrative accounts.
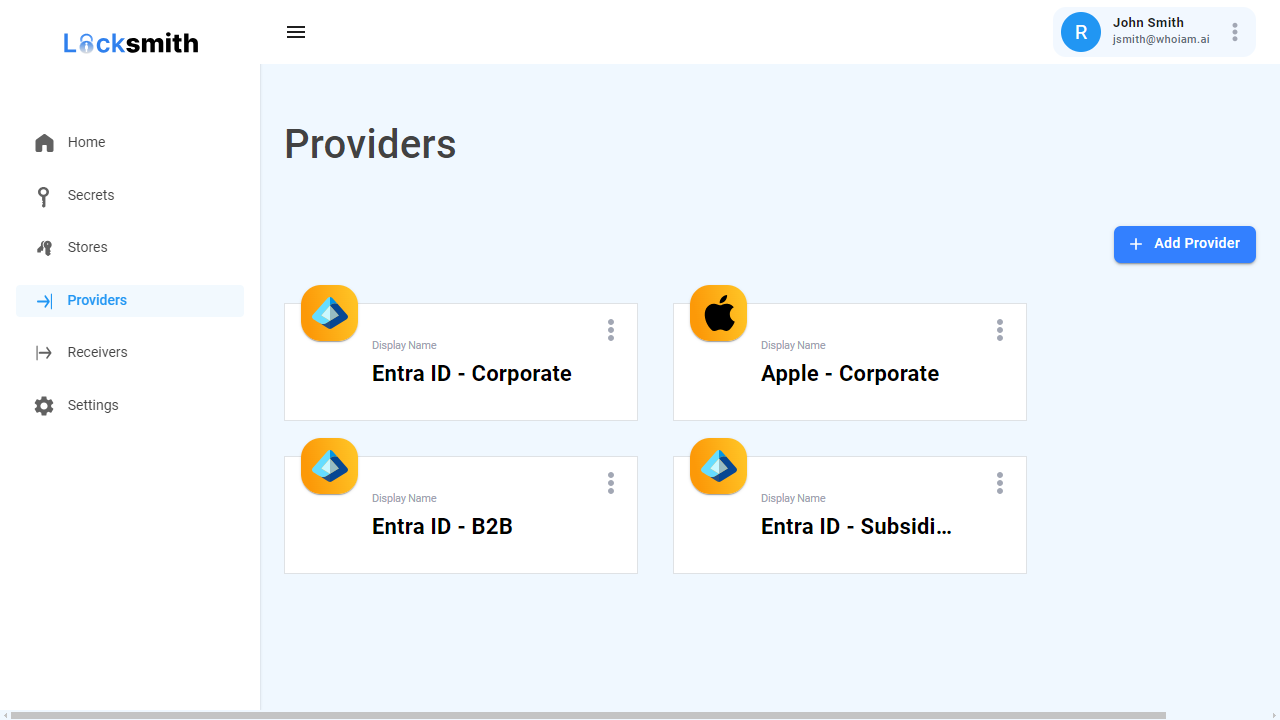
WhoIAM Locksmith helps you implement a robust secret rotation strategy by monitoring secrets within Azure Key Vault, notifying administrators when they are due to expire, and replacing them under reliable rotation schedules. It also connects to systems within multiple platforms (including Microsoft and Apple) to update their configurations as part of the secret rotation process.